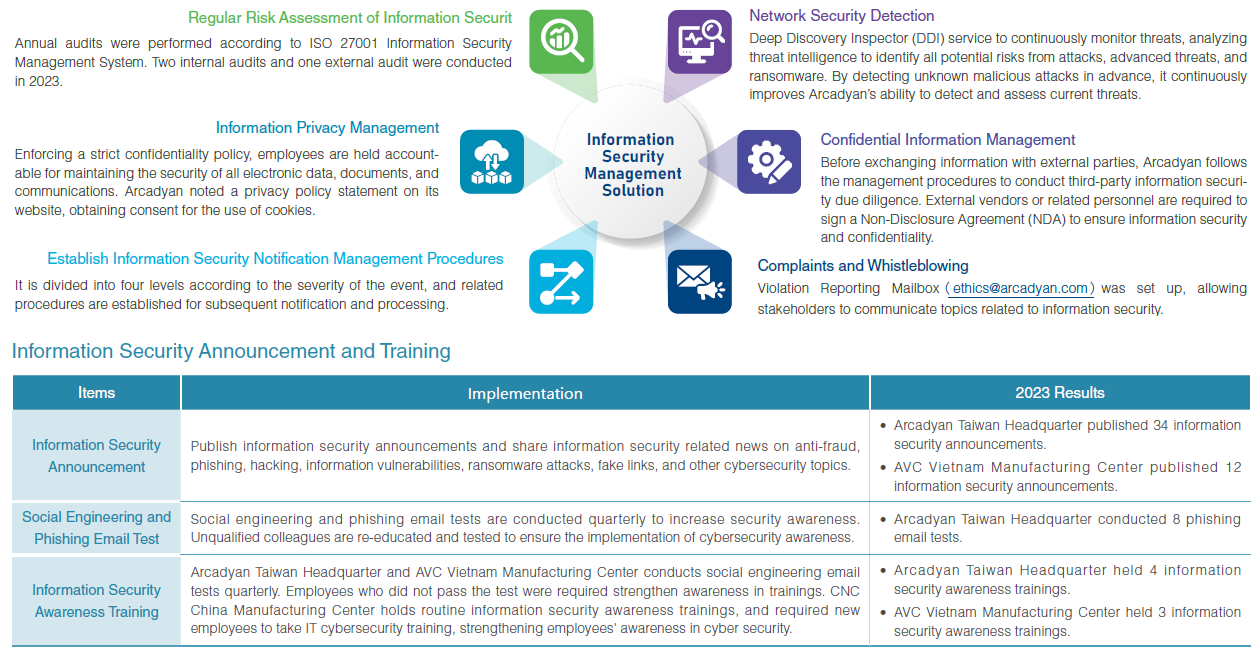
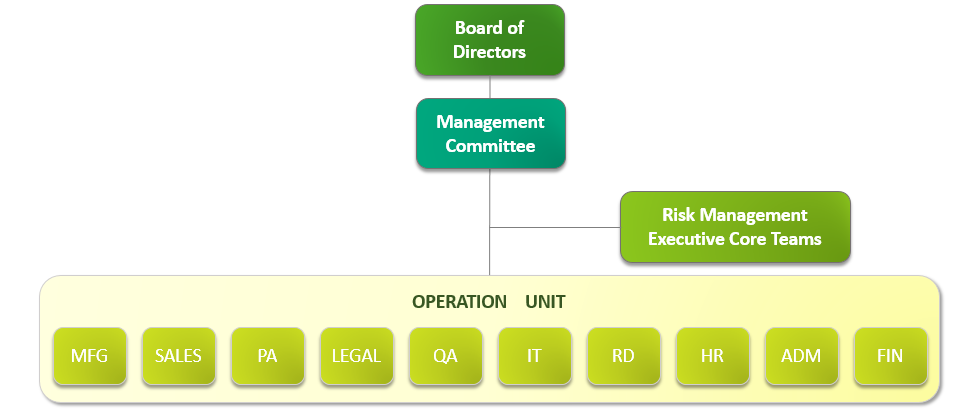
To establish a comprehensive risk management structure, Arcadyan Board Directors approved Risk Management Policy and Procedure on November 10, 2022. The Policy and Procedure is to create a risk-award culture, assist the management to make informed business decisions and stabilize business operations toward corporate sustainability.
Based on company size, industry type, business characteristics, operation activities, and taking core values of corporate sustainability into consideration, Arcadyan has identified risk factors including strategic, operational, financial, information, compliance, integrity and other new emerging risks (e.g. climate change or infectious disease.) The nature and characteristics of identified risk events are studied, and the probability of the occurrence and impact level are analyzed, and further response measures are planned referring to the risk assessment conducted.
Arcadyan ISO 22301 Business Continuity Management Policy
- Effectively manage any unforeseen events that could potentially disrupt
company operations. - Ensure that critical products and services are restored to customers within the agreed-upon timeframe in the event of an operational disruption.
- Minimize potential impacts of any operational disruptions on Arcadyan
and its reputation.
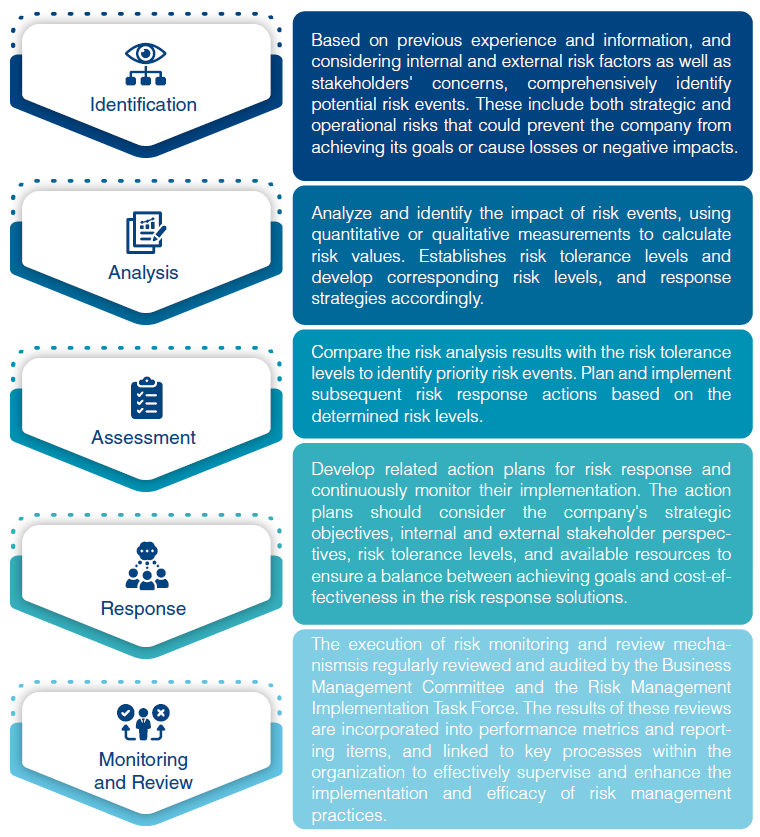
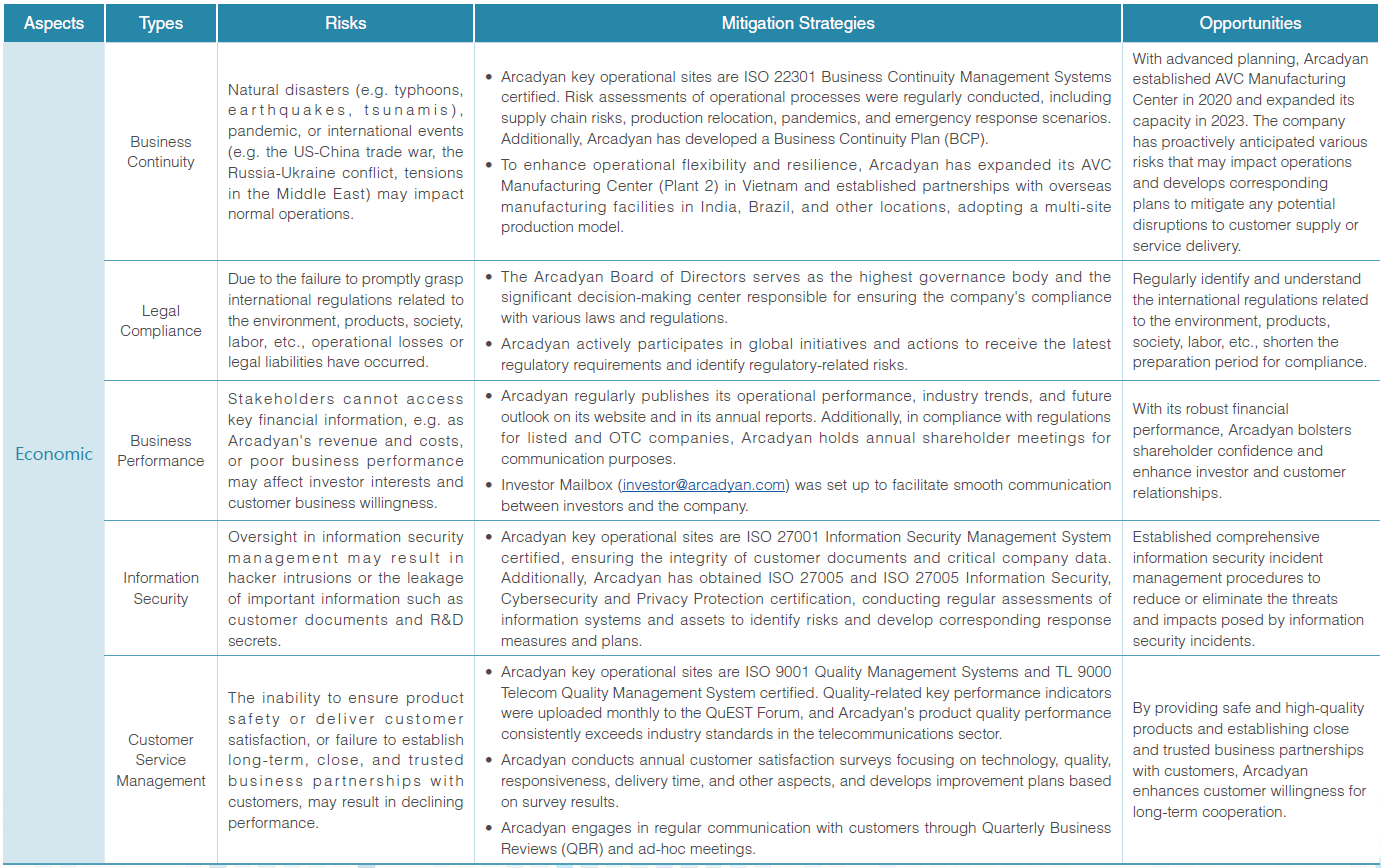
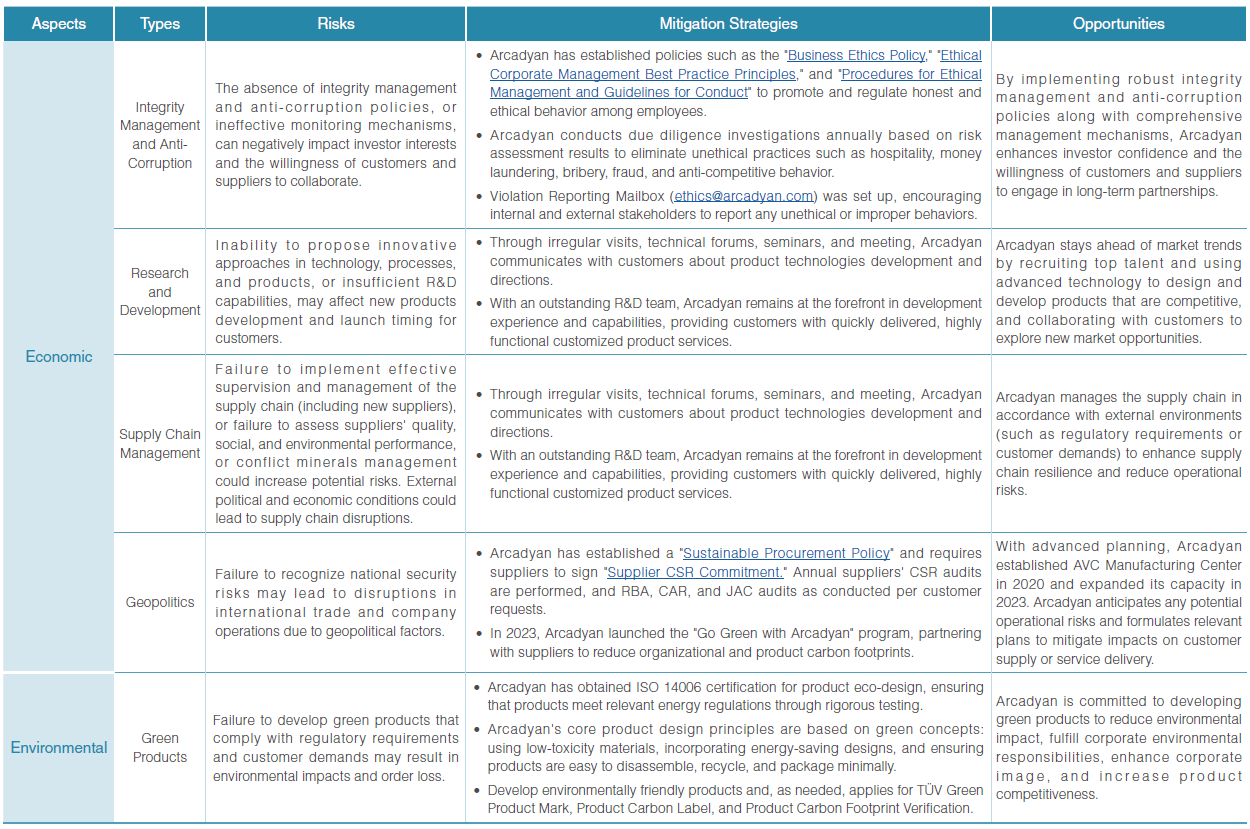
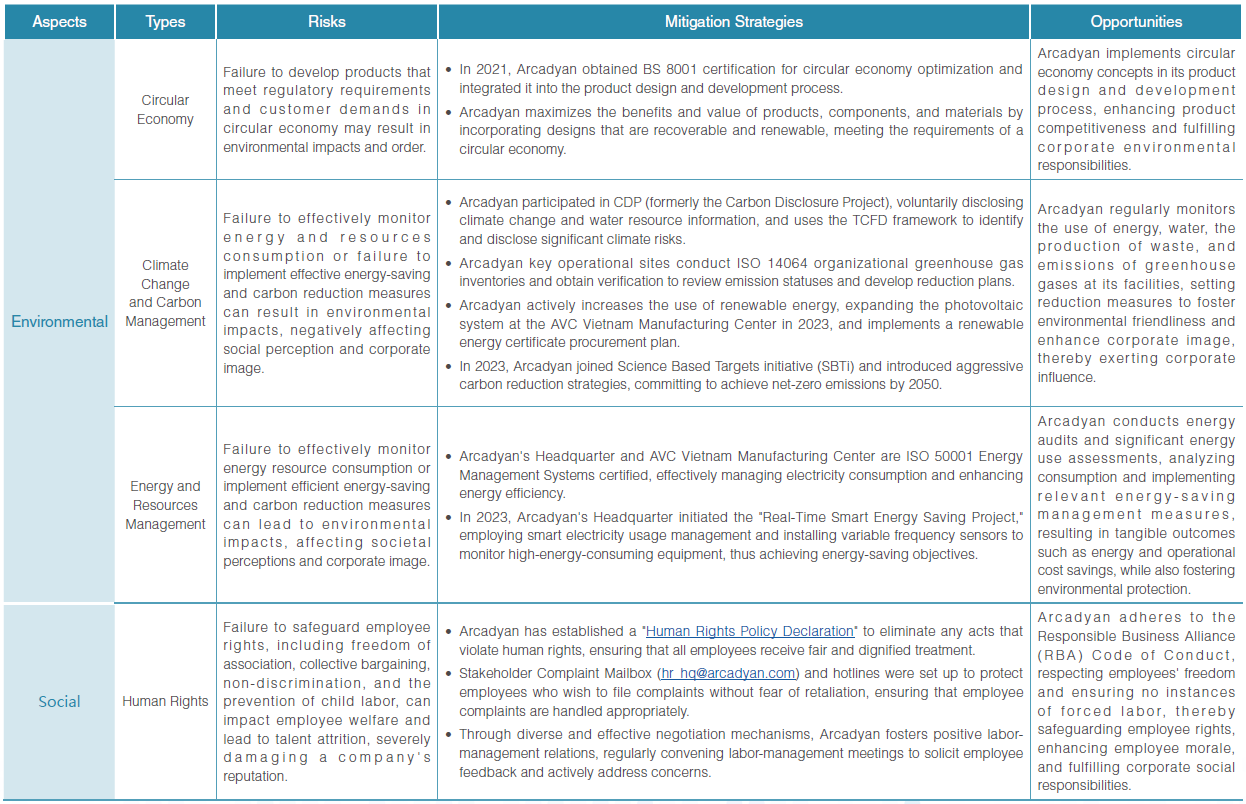
Arcadyan's headquarters and overseas manufacturing centers obtain ISO 22301 Business Continuity Management System certification annually. They establish processes for analysis and risk assessment, evaluating the frequency and likelihood of risks based on the PPTISSFT (People, Premises, Technology, Information, Stakeholders, Suppliers, Finance, and Transportation) of critical activities. Recovery priorities, an Incident Management Plan (IMP), and a Business Continuity Plan (BCP) are set up to effectively manage any unforeseen events that could potentially disrupt Arcadyan's operations. In 2023, risk management and response strategies were developed based on key sustainability issues, as detailed below:
Arcadyan ISO 27001 Information Security Management Policy
- Ensure the confidentiality of information related to the business of the Company to prevent breaches or losses of the Company's sensitive information and individual data.
- Ensure the completeness and availability of the Company's business information to perform the operation and various business of the Company correctly.
To ensure the confidentiality, integrity, and availability of all information, Arcadyan follows the ISO/IEC 27001 international standard to establish internal control documents. Annually, internal and external audits are conducted to evaluate the risk levels of various process databases, scan system vulnerabilities, update information asset inventories, and execute related operational impact analyses, disaster recovery drills, user account privilege reviews, firewall configuration reviews, information security awareness and education training, penetration testing, governance committee meetings, and periodic social media exercises as control mechanisms.